Read More

With 20+ years in technical roles and specialized GRC expertise, I translate complex security frameworks into actionable insights. My journey from financial compliance to enterprise security initiatives informs this blog, where I break down cybersecurity concepts for both professionals and everyday users seeking practical protection in our digital world.
Thursday, October 5, 2017
It’s time to give Firefox another chance | TechCrunch
Read More
Equifax breach shows signs of a possible state-sponsored hack
Read More
One third of smartphone notifications make our mood worse, research shows??
As part of the study, the researchers developed an app – NotiMind – which participants downloaded to their phones. The app collected details relating to the phone’s digital notifications, as well as participants’ self-reported moods at various points in the day over a five-week period.
The researchers say their findings show that it possible to predict phone users’ moods based on information they are receiving. ?? In the future they say it could be used to personalise notifications, so fewer system notifications were sent when someone was feeling down, or more entertainment features to boost mood.
Read More
How a missing smiley foiled a $70,000 email fraud
|
Friday, September 29, 2017
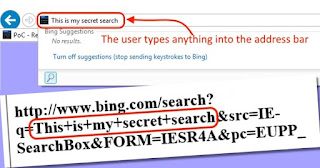
Internet Explorer bug can reveal the contents of your address bar – HOTforSecurity
If you’re one of the many people still using Microsoft Internet Explorer to surf the internet, you have just been given another good reason to upgrade to a more modern browser.
Read More:
Internet Explorer bug can reveal the contents of your address bar – HOTforSecurity
Friday, September 8, 2017
Avoiding Social Engineering and Phishing Attacks
What is a social engineering attack?
In a social engineering attack, an attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems. An attacker may seem unassuming and respectable, possibly claiming ... READ MORE
Using Caution with Email Attachments
Why can email attachments be dangerous?
Some of the characteristics that make email attachments convenient and popular are also the ones that make them a common tool for attackers:
- Email is easily circulated – Forwarding email is so simple that viruses can quickly infect many machines. Most viruses don't even require users to forward the email—they scan a users' computer for email addresses ...
Subscribe to:
Posts (Atom)
-
The Windows logo key, located in the bottom row of most computer keyboards is a little-used treasure. Don't ignore it. It is the shortcu...
-
Open Paint by clicking the Start button, clicking All Programs, clicking Accessories, and then clicking Paint. Click the Paint button, cli...
-
By: Fahmida Y. Rashid 2010-09-27 Cisco Systems says spammers targeted LinkedIn members with fake connection requests that downloaded a wo...