
Carly’s phone buzzed with a notification that made her heart skip a beat. “RealCelebAssist_Jane has sent you a message.” Her favorite actor’s assistant had actually reached out to her! She’d been following his career for years, attending premieres when possible and engaging thoughtfully with his social media posts. But this… this was different.
“Hello Carly!” the message read. “I’ve noticed you’re the biggest fan of [celebrity name]. He’s really impressed by your dedication and support!”
Carly’s fingers trembled as she typed her response. Could this really be happening? The conversation flowed easily at first, with Jane sharing small details about the celebrity’s day-to-day life that weren’t public knowledge. Or at least, Carly thought they weren’t.
“I’d love to show you what he thinks about you,” Jane wrote. “But I can’t send pictures in DMs. Could you share your email?”

That’s when the first shadow of doubt crept in. Carly knew perfectly well that DMs could handle pictures. Still, swept up in the possibility of connecting with her idol, she created a secondary email address and shared it.
The email arrived from “jane.assisstant.celeb@gmail.com” — the misspelling subtle but present. The header showed traces of Yahoo, despite the Gmail address. Inside were screenshots of supposed conversations, each one making Carly’s heart race faster, but not from excitement anymore.

“He’d love to chat with you directly,” Jane wrote. “Just download Signal and…”
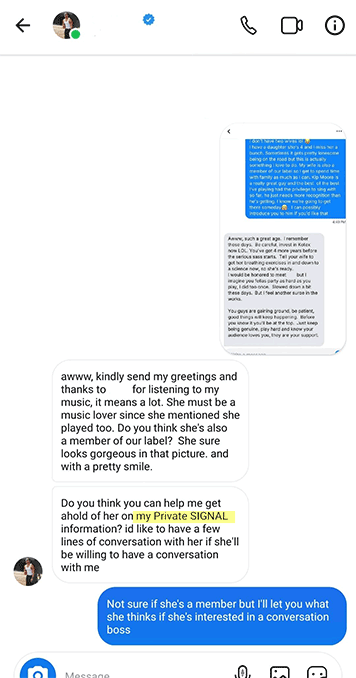
Carly sat back in her chair, the fantasy crumbling around her. Signal. The same app her friend Sarah had mentioned when describing how she’d lost thousands to a romance scam last year. The pieces started falling into place: the rushed intimacy, the technical excuses, the push to move platforms.
She thought about the real celebrity, probably relaxing in his actual home, completely unaware of how his image was being used to manipulate fans. She thought about how close she’d come to falling for it, how the excitement had almost overwhelmed her natural skepticism.
Opening her laptop, Carly began documenting everything: screenshots of the conversations, the email headers, the inconsistencies. She reported the account to the platform and drafted a post warning other fans about the scam. Maybe the next person would recognize the red flags sooner.
As she blocked the scammer’s accounts, Carly felt not disappointment, but pride. She’d trusted her instincts, protected herself, and now she could help protect others. The real connection she’d hoped for hadn’t materialized, but she’d gained something equally valuable: wisdom she could share with her community.
That night, scrolling through her favorite celebrity’s verified Instagram account, Carly smiled at his latest post — a simple behind-the-scenes photo from his new project. This was the real connection: appreciating his work from a respectful distance, no intermediaries or secret channels required. Sometimes the most authentic fan experience is simply being a fan, nothing more, nothing less.
And somewhere in the digital ether, “Jane” moved on to her next target, unaware that her failed attempt with Carly would help countless others recognize the same scam before it was too late.

The red flags Carly identified are spot-on:
- Claiming inability to send pictures in DMs (a false technical limitation)
- A “celebrity assistant” randomly reaching out to fans
- Mismatched email domains and misspellings
- Pushing to move communication to Signal
If Carly continued engaging, here’s the likely progression:
- Trust Building Phase
- The “assistant” would likely share more fabricated screenshots and insider details
- The “celebrity” would eventually start direct communication
- They’d build emotional connection through flattery and “exclusive” attention
- They’d emphasize keeping the relationship secret “to protect privacy”
2. The Setup
- After establishing trust, they’d likely manufacture an urgent situation
- Common scenarios include:
- Claiming to need help with a confidential investment opportunity
- Having assets frozen and needing temporary financial assistance
- Offering to send Carly gifts/money but needing fees paid first
- Claiming to need help moving funds internationally
3. Financial Exploitation
- Requests would start small to test compliance
- They’d use urgency and emotional manipulation
- They might request gift cards (harder to trace)
- Could ask for bank account details for “sending money”
- Might request personal information for identity theft
To protect yourself from celebrity impersonation scams:
- Verify Communication Channels
- Check if the celebrity has verified social media accounts
- Real celebrities/assistants use official channels, not personal emails
- Be wary of platform-hopping (moving between different apps/services)
2. Question the Narrative
- Consider why a celebrity would reach out randomly
- Be skeptical of requests for secrecy
- Watch for inconsistencies in stories
- Remember that real celebrities don’t need fans’ financial help
3. Protect Your Information
- Never share financial account details
- Don’t send money or gift cards
- Keep personal information private
- Don’t share identification documents
- Be wary of requests to download specific apps
If you encounter such a scam:
- Report the accounts to the platform
- Save screenshots of conversations (as evidence)
- Report to relevant authorities
- Block all contact methods
- Alert others in fan communities about the scam pattern

Looking to bring your story to life? I’m a professional writer, ghostwriter and cybersecurity expert available for creative and commercial projects. Let’s collaborate on making your vision a reality. Learn More About Me, I’d love to know how I may help you with your current or next project.


No comments:
Post a Comment