Just when you get settled on blaming Chrome, or Firefox, or Edge and the hundreds of tabs you may have open for slowing your computer down ... now you're validated!
While this is an insidious and violating happenstance, don't worry, once this fad is vanquished, there'll be others.
This article was originally found at: ArsTechnica
Cryptojacking craze that drains your CPU now done by 2,500 sites
Android apps with millions of Google Play downloads also crash the party.
A researcher has documented almost 2,500 sites that are actively running cryptocurrency mining code in the browsers of unsuspecting visitors, a finding that suggests the unethical and possibly illegal practice has only picked up steam since it came to light a few weeks ago.
Willem de Groot, an independent security researcher
who reported the findings
Tuesday, told Ars that he
believes all of the 2,496 sites he tracked are running out-of-date software with
known security vulnerabilities that have been exploited to give attackers
control. Attackers, he said, then used their access to add code that
surreptitiously harnesses the CPUs and electricity of visitors to generate the
digital currency known as Monero. About 80 percent of those sites, he added,
also contain other types of malware that can steal visitors' payment card
details.
"Apparently, cyberthieves are squeezing every penny out of their
confiscated assets," he said.
One of the affected sites is shop.subaru.com.au. When I
visited the site on Tuesday, the fan on my MacBook Pro, which I hadn't heard in
months, soon started whirring. The activity monitor showed that about 95 percent
of the CPU load was being consumed. As soon as I closed the site, the load
dropped to about 9 percent. Besides putting a noticeable strain on my computer,
the site also draws additional electricity from my office. The arrangement
allows the attackers to reap the benefit of my hardware and electricity without
providing anything to me in return. A recent report from security firm Trustwave's
SpiderLabs estimated that the
electricity cost for a single computer could range from about $2.90 to $5 per
month, presumably if the cryptomining page was left open and running
continuously over that time. The figure doesn't include the wear and tear on
hardware as it performs complex mathematical problems required to generate the
digital coins.
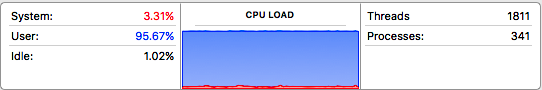
Activity monitor showing CPU load when visiting
http://shop.subaru.com.au.
Thanks, Coinhive
The site that makes all of this possible is Coinhive.com,
which Ars covered last week. It offers an easy-to-use programming interface that any website
can use to turn visitors' computers into vehicles for generating—or in the
parlance of cryptocurrency people, mining—Monero. Coinhive gives participating
sites a tiny cut of the proceeds and pockets the rest. Coinhive doesn't require
that sites provide any notice to users.
de Groot said that about 85 percent of the 2,496 sites he tracked
are generating currency on behalf of just two Coinhive accounts. Depending on
the total number of visitors, the amount of time they stay on an affected site,
and the power of their computers, the revenue collected by those accounts could
be considerable, as would be the total amount of additional charges those
accounts made to visitors' electric bills. The remaining 15 percent were spread
over additional Coinhive accounts, but de Groot has evidence suggesting those
accounts are controlled by a single individual or group. Most of the affected
sites concealed the connection to Coinhive by adding a link to the domain
siteverification.online or one masquerading as a Sucuri firewall. Those
disguised sites, in turn, hosted the crypto-mining JavaScript that interacted
with Coinhive.
de Groot's findings suggest that drive-by cryptomining has grown
more widespread in the week since Ars first covered it or at least that the
phenomenon shows no signs of abating. The earlier Ars article cited research
from security firm Sucuri that found 500 sites running hacked versions of the
WordPress content management system that were participating in the Coinhive
mining. Ars also reported that two Android apps with as many as 50,000 downloads
from Google Play had recently been caught putting cryptominers inside hidden
browser windows. On Wednesday, researchers from Ixia
reported finding two additional such apps with as many
as 15 million downloads combined. (In fairness, one of the apps
informed users it would use their phone's idle time to generate coins and
provided a way for that default setting to be turned off. The apps have since
been modified to curtail the practice.)
There are other indications that the in-browser cryptomining
racket is getting worse. In a report published Tuesday, endpoint security provider Malwarebytes said that on average it
performs about 8 million blocks per day to unauthorized mining pages.
People who want to avoid these cryptojacking scams can use
Malwarebytes or another antivirus program that blocks abusive pages,
install this Chrome extension, or update their computer host file to block coinhive.com and other sites known to
facilitate unauthorized mining. As the phenomenon continues to grow and attract
copycat services, blocklists will likely have to be updated, requiring regular
updates to blocklists as
well.



No comments:
Post a Comment